WP: How to achieve 400 UPH with Locus Fast Pick
WP: How to achieve 400 UPH with Locus Fast Pick Download Now!
Top Warehouse Automation Security Topics to Discuss with a Vendor
Fouad Khalil, Sr. Dir., Ent. Security, Risk & Compliance

As digital threats loom larger than ever, automating your warehouse is not just about enhancing operational efficiency — it’s equally about safeguarding your digital and physical assets. The relentless rise in cyber threats such as ransomware and phishing attacks underscores the imperative need for robust security measures, especially in sectors as vital as warehousing and logistics. As warehouses evolve from manual to automated systems, the security of these solutions cannot be an afterthought. It must be a foundational aspect of any automation implementation.
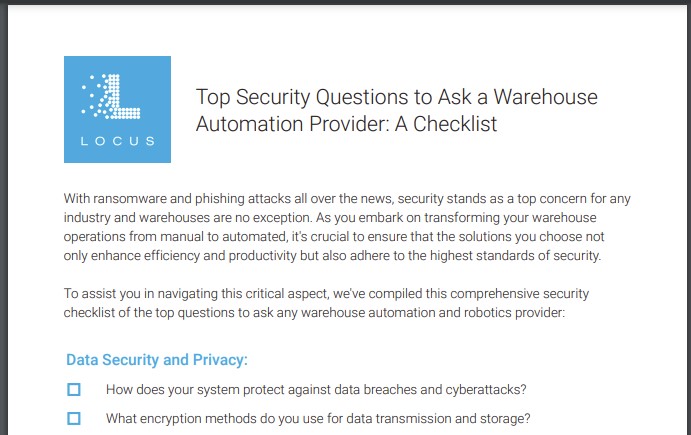
This necessity brings us to the heart of the reason for this blog: The top security questions you should ask a warehouse automation provider (Note: Clicking on this title will open up the PDF of the checklist). This checklist not only serves as a guide but as a means to ensure that the solutions you select are fortified with the highest security standards, protecting your operations from the myriad of digital threats existing today.
Data Security and Privacy: The First Line of Defense
The sanctity of your data — be it related to operations, employees, or customers — cannot be compromised. Engaging with your provider on their data protection mechanisms is crucial. Queries regarding their defense strategies against data breaches, the encryption protocols employed for safeguarding data during transmission and storage, and adherence to privacy regulations like HIPAA, GDPR, or CCPA are non-negotiable. Understanding where your data resides and the measures in place for at-risk data is foundational to securing your operations against external threats.
Network Security Measures: Ensuring a Fortified Network
The network is the backbone of any automated warehouse system. It’s imperative to delve into the specifics of the network security measures the provider has implemented. Discussing whether the robotics systems come with a dedicated Wi-Fi network, which can operate securely without interfering or being impacted by your existing network infrastructure, is vital for maintaining a secure and efficient operational environment.
Access Control and Authentication: Who Has the Keys?
Robust access control mechanisms and user authentication protocols are essential to prevent unauthorized access to the system. It’s important to inquire about the presence of multi-factor authentication, authorization levels for different users, and the processes for onboarding and offboarding access. These layers of security ensure that only authorized personnel can access sensitive operational data and control the automated systems.
Compliance with Industry Standards: A Badge of Trust
Adherence to relevant security regulations and standards is a testament to a provider’s commitment to security. Asking for documentation or certifications of compliance can give you peace of mind and serve as proof of the provider’s dedication to maintaining high-security standards.
Physical Security of Robots: Beyond the Digital Realm
The security conversation often revolves around digital threats, but the physical security of the robots themselves is equally crucial. Inquiring about the built-in physical security features that prevent tampering or unauthorized access to the robots is important. Understanding how the robots are monitored for potential security breaches adds another layer of assurance.
Incident Response and Recovery: Preparing for the Worst
Despite all precautions, incidents may occur. It’s critical to discuss the provider’s protocol for responding to security incidents, their incident response plan, and their disaster recovery and business continuity strategies. These discussions ensure that, in the event of a security breach, both immediate and long-term responses are swift and effective, minimizing potential damage and downtime.
Employee Training and Awareness: Cultivating a Culture of Security
The human element cannot be overlooked in the security equation. Understanding the training provided by the provider to ensure their staff adheres to security best practices, as well as any training offered for your employees, is essential. This not only enhances the security of the automated systems but also fosters a culture of security within your organization.
Security as a Partnership
Navigating the security landscape of warehouse automation is a complex but necessary endeavor. By engaging potential automation providers with these critical security questions, you can establish a dialogue that places security at the forefront of your automation journey. This proactive approach not only protects your operations but also builds a foundation of trust and reliability with your provider.
At Locus Robotics, we understand the criticality of security in the automation space. Our commitment to safeguarding our autonomous mobile robots (AMRs) and the systems that support them is unwavering. We are dedicated to ensuring that our solutions not only meet but exceed the security expectations of our clients, offering peace of mind in an increasingly digital world. Download the checklist and then contact us to explore how our secure, innovative automation solutions can transform your warehouse operations, ensuring efficiency, productivity, and, most importantly, security.
About the Author
As Senior Director, Compliance at Locus Robotics, Fouad is responsible for internal and external compliance programs, auditor education, alignment with industry best practices and cross-functional support. He brings extensive experience in the technology space with more than 25 years spanning disciplines in software development, IT support, program and project management and most recently IT Security and Compliance management. Khalil’s career path in technology has provided him with keen insights in the areas of network, system and database administration, software programming, system, software and GUI design, project and product development, solution implementation and much more. For nearly the past two decades, Khalil has focused on data security, security investigations, cybersecurity, security training and awareness, and security compliance– serving as an industry expert in key areas such as IT, NIST, Internal Controls over financial reporting, Sarbanes-Oxley, GDPR, CCPA, PCI DSS, HIPAA and HITECH. Khalil holds a Bachelor’s degree in Electrical and Computer Engineering from Marquette University and CISA, CDPSE and ITIL Foundations certifications. Additionally, he is an active member/contributor in ISACA, IIA and Infragard.